Breadcrumb
An Efficient DMO Task Scheduling Technique for Wearable Biomedical Devices
The popularity of wearable devices has grown as they improve the quality of life in many applications. In particular, for medical devices, energy harvesters are the dominating source of energy for wearable devices. However, their power budget is limited. Thus, power-saving techniques are essential components in the whole technology stack of those devices. That is, choosing the optimal schedule for different tasks running on the wearable device can help to reduce energy consumption. This paper presents a sensor task scheduling technique for optimizing energy consumption for energy harvesting
Light-Weight Face Mask Detector
People's lives have been severely disrupted recently due to the COVID-19 outbreak's fast worldwide proliferation and transmission. An option for controlling the epidemic is to make individuals wear face masks in public. For such regulation, automatic and effective face detection systems are required. A facial mask recognition model for real-time video-recorded streaming is provided in this research, which categorizes the pictures as (with mask) or (without mask). A dataset from Kaggle was used to develop and assess the model. The suggested system is computationally more precise, efficient and
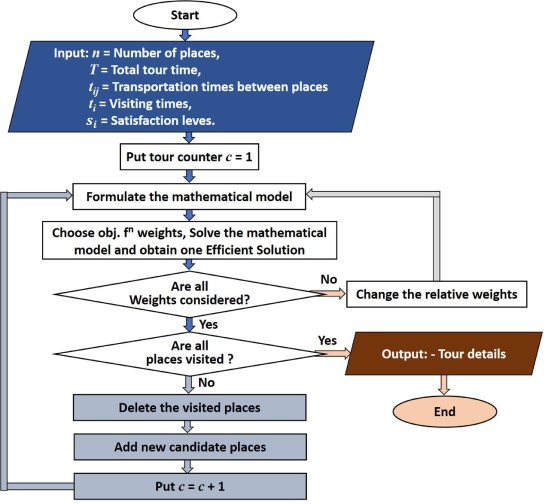
A multiobjective nonlinear combinatorial model for improved planning of tour visits using a novel binary gaining-sharing knowledge- based optimization algorithm
This chapter proposes a novel binary version of recently developed Gaining-Sharing knowledge-based optimization algorithm (GSK) to solve binary optimization problems. GSK algorithm is based on the concept of how humans acquire and share knowledge during their life span. Binary version of GSK named novel binary Gaining-Sharing knowledge-based optimization algorithm (BGSK) depends on mainly two binary stages: binary junior gaining sharing stage and binary senior gaining sharing stage with knowledge factor 1. These two stages enable BGSK for exploring and exploitation of the search space
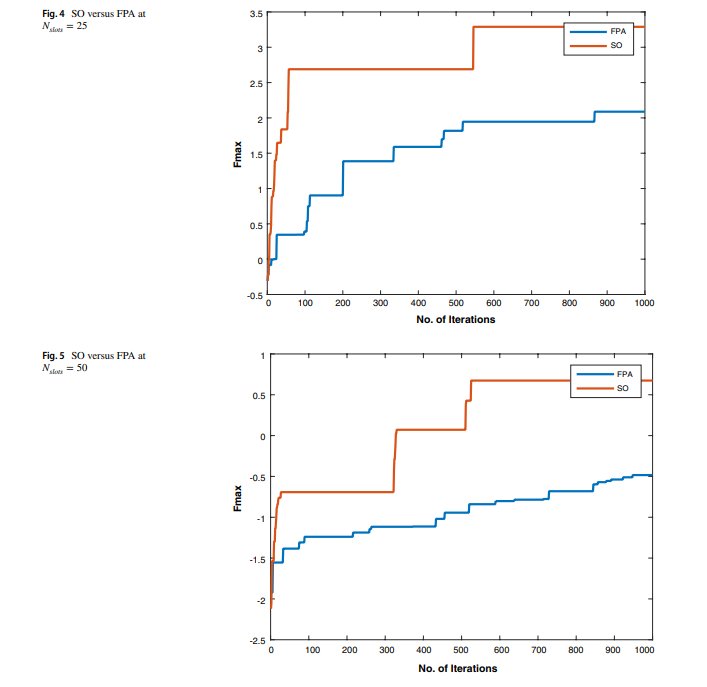
A power-aware task scheduler for energy harvesting-based wearable biomedical systems using snake optimizer
There is an increasing interest in energy harvesting for wearable biomedical devices. This requires power conservation and management to ensure long-term and steady operation. Hence, task scheduling algorithms will be used throughout this work to provide a reliable solution to minimize energy consumption while considering the system operation constraints. This study proposes a novel power-aware task scheduler to manage system operations. For example, we used the scheduler to handle system operations, including heart rate and temperature sensors. Two optimization techniques have been used to

Downlink Throughput Prediction in LTE Cellular Networks Using Time Series Forecasting
Long-Term Evolution (LTE) cellular networks have transformed the mobile business, as users increasingly require various network services such as video streaming, online gaming, and video conferencing. A network planning approach is required for network services to meet user expectations and meet their needs. The User DownLink (UE DL) throughput is considered the most effective Key Performance Indicator (KPI) for measuring the user experience. As a result, the forecast of UE DL throughput is essential in network dimensioning for the network planning team throughout the network design stage. The
Light-Weight Face Shape Classifier for Real-Time Applications
Deep neural networks (DNNs) are memory and computationally intensive; hence they are difficult to apply to real-time systems with limited resources. Therefore, the DNN models need to be carefully optimized. The solution was a model based on a convolutional neural network (CNN) called MobileNet that decreases the computational and space complexities with classification precision loss by utilizing depthwise separable convolutions. This study uses MobileNet vl architecture to improve image classification complexities to reach an acceptable complexity that can be used in real-time applications
A Generic AI-Based Technique for Assessing Student Performance in Conducting Online Virtual and Remote Controlled Laboratories
Due to the COVID-19 pandemic and the development of educational technology, e-learning has become essential in the educational process. However, the adoption of e-learning in sectors such as engineering, science, and technology faces a particular challenge as it needs a special Laboratory Learning Management System (LLMS) capable of supporting online lab activities through virtual and controlled remote labs. One of the most challenging tasks in designing such LLMS is how to assess a student's performance while an experiment is being conducted and how stuttering students can be automatically

Stability Analysis and Fault Detection of Telecommunication Towers Using Decision Tree Algorithm under Wind Speed Condition
This paper presents a decision tree (DT) modeling technique to estimate any increase in the load on telecommunication towers. A structural analysis was done for the lattice and mono-pole towers using TNX Tower software to determine the basic features of the towers, such as tilt angle, deflection, twist, and acceleration. The structure analysis generated a data set based on wind speeds. This data set was then used to train a machine-learning algorithm to estimate the loads on the structure. Any change in the applied loads greater than the loads considered in the design might be identified using

Indoor Air Quality Monitoring Systems for Sustainable Medical Rooms and Enhanced Life Quality
Indoor air pollution poses a substantial risk to human health and well-being, underscoring the crucial requirement for efficient monitoring systems. This paper introduces an advanced Air Pollution Monitoring System (APMS) tailored explicitly for indoor settings. The APMS integrates sensors and a user interface, ensuring the delivery of real-time and precise data concerning air quality parameters such as particulate matter (PM), volatile organic compounds (VOCs), carbon dioxide (CO2), as well as temperature and humidity. The proposed APMS has several advantages, including low maintenance

In the Identification of Arabic Dialects: A Loss Function Ensemble Learning Based-Approach
The automation of a system to accurately identify Arabic dialects many natural language processing tasks, including sentiment analysis, medical chatbots, Arabic speech recognition, machine translation, etc., will greatly benefit because it’s useful to understand the text’s dialect before performing different tasks to it. Different Arabic-speaking nations have adopted various dialects and writing systems. Most of the Arab countries understand modern standard Arabic (MSA), which is the native language of all other Arabic dialects. In this paper we propose a method for identifying Arabic dialects
Pagination
- Previous page ‹‹
- Page 3
- Next page ››
