Breadcrumb
CellNet:A bottom-up approach to network design
The ever-increasing dependence on the Internet is challenged by several factors impeding the smooth transition to the nomadic and ubiquitous future communications. These hindering factors are primarily attributed to the top-down approach in designing computer networks that resulted in adopting a layered architecture for abstracting network functionalities as well as for engineering protocols; a methodology that proved to be neither adaptable nor evolvable in response to changes in network operational requirements and technological advancements. This paper presents a bottom-up1 strategy for
Cooperative D2D communication in downlink cellular networks with energy harvesting capability
Device-to-Device (D2D) communications have been highlighted as one of the promising solutions to enhance spectrum utilization of LTE-Advanced networks. In this paper, we consider a D2D transmitter cooperating with a cellular network by acting as a relay to serve one of the cellular users. We consider the case in which the D2D transmitter is equipped with an energy harvesting capability. We investigate the trade-off between the amount of energy used for relaying and the energy used for decoding the cellular user data at the relaying node. We formulate an optimization problem to maximize the
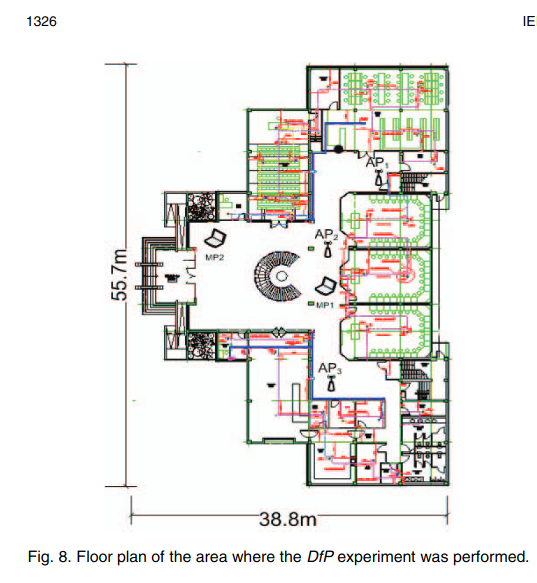
Nuzzer: A large-scale device-free passive localization system for wireless environments
The widespread usage of WLANs and mobile devices has fostered the interest in localization systems for wireless environments. The majority of research in the context of wireless-based localization systems has focused on device-based active localization, in which devices are attached to tracked entities. Recently, device-free passive localization (DfP) has been proposed where the tracked entity is neither required to carry devices nor to participate actively in the localization process. Previous studies have focused on small areas and/or controlled environments. In this paper, we present the
CellSense: An accurate energy-efficient GSM positioning system
Context-aware applications have been gaining huge interest in the last few years. With cell phones becoming ubiquitous computing devices, cell phone localization has become an important research problem. In this paper, we present CellSense, which is a probabilistic received signal strength indicator (RSSI)-based fingerprinting location determination system for Global System for Mobile Communications (GSM) phones. We discuss the challenges of implementing a probabilistic fingerprinting localization technique in GSM networks and present the details of the CellSense system and how it addresses
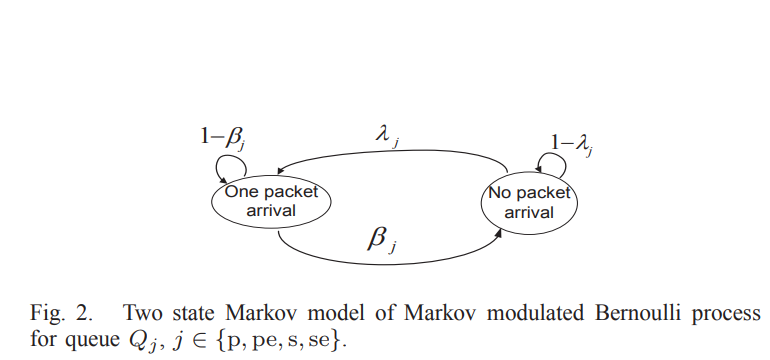
Optimal cooperative cognitive relaying and spectrum access for an energy harvesting cognitive radio: Reinforcement learning approach
In this paper, we consider a cognitive setting under the context of cooperative communications, where the cognitive radio (CR) user is assumed to be a self-organized relay for the network. The CR user and the primary user (PU) are assumed to be energy harvesters. The CR user cooperatively relays some of the undelivered packets of the PU. Specifically, the CR user stores a fraction of the undelivered primary packets in a relaying queue (buffer). It manages the flow of the undelivered primary packets to its relaying queue using the appropriate actions over time slots. Moreover, it has the
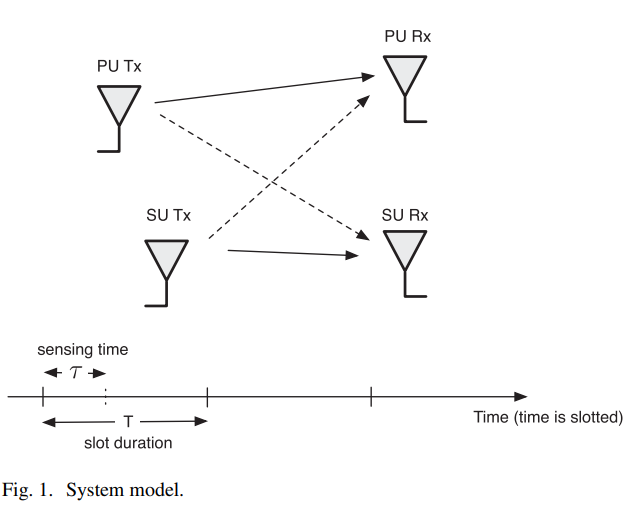
Effective capacity of delay-constrained cognitive radio links exploiting primary feedback
In this paper, we study the effective capacity (EC) of cognitive radio (CR) networks operating under statistical quality-of-service (QoS) constraints in an attempt to support real-time applications at the secondary users (SUs). In particular, we analyze the performance gains, in terms of EC and average transmitted power, attributed to leveraging the primary user (PU) feedback overheard at the SU, at no additional complexity or hardware cost. We characterize the EC performance improvement for the SU, in the presence of a feedback-based sensing scheme, under the signal-to-interference-plus-noise

On optimal policies in full-duplex wireless powered communication networks
The optimal resource allocation scheme in a full-duplex Wireless Powered Communication Network (WPCN) composed of one Access Point (AP) and two wireless devices is analyzed and derived. AP operates in a full-duplex mode and is able to broadcast wireless energy signals in downlink and receive information data in uplink simultaneously. On the other hand, each wireless device is assumed to be equipped with Radio-Frequency (RF) energy harvesting circuitry which gathers the energy sent by AP and stores it in a finite capacity battery. The harvested energy is then used for performing uplink data
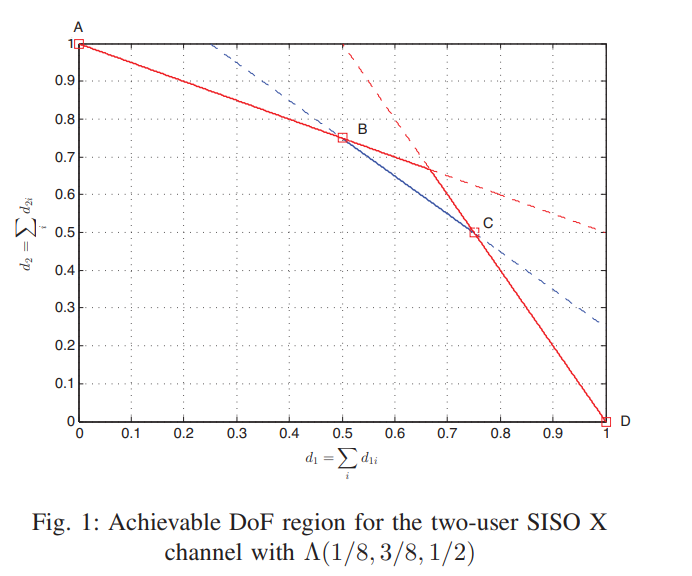
On the synergistic benefits of alternating CSIT for X channel within a four-symbol channel extension
In this paper, we investigate the degrees of freedom (DoF) of the two-user single input single output (SISO) X channel with alternating channel state information at the transmitters (CSIT). Three cases are considered for the availability of CSIT; perfect, delayed and no-CSIT. Each state is associated with a fraction of time denoted by λP, λD and λN, respectively. We provide new results for the achievable DoF of the channel when the available CSIT alternates between these three cases under a certain distribution for Λ(λP, λD, λN). Specifically, we show that the two-user SISO X channel with
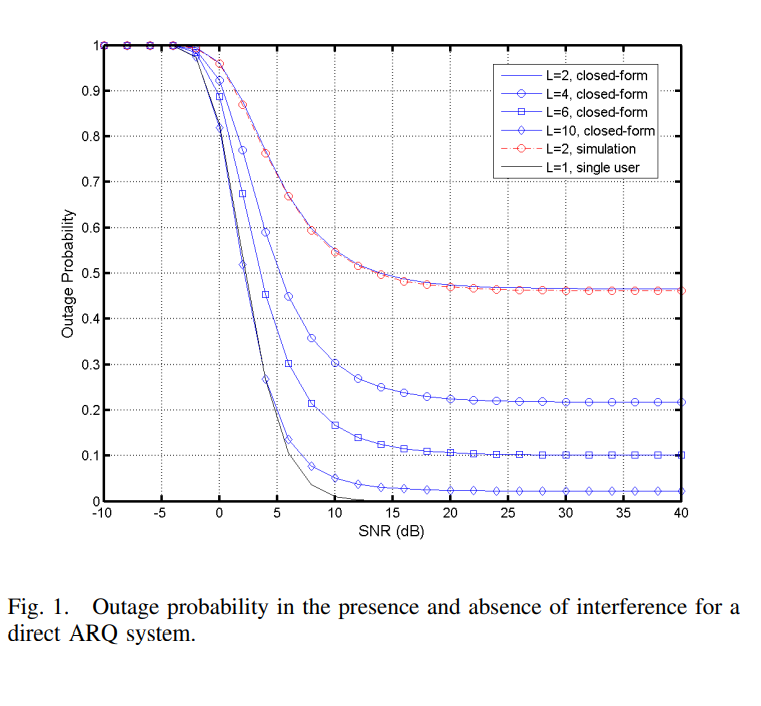
Optimal beamforming for MIMO shared relaying in downlink cellular networks with ARQ
In this paper, we study the performance of the downlink of a cellular network with automatic repeat-request (ARQ) and a half duplex decode-and-forward shared relay. In this system, two multiple-input-multiple-output (MIMO) base stations serve two single antenna users. A MIMO shared relay retransmits the lost packets to the target users. First, we study the system with direct retransmission from the base station and derive a closed form expression for the outage probability of the system. We show that the direct retransmission can overcome the fading, however, it cannot overcome the
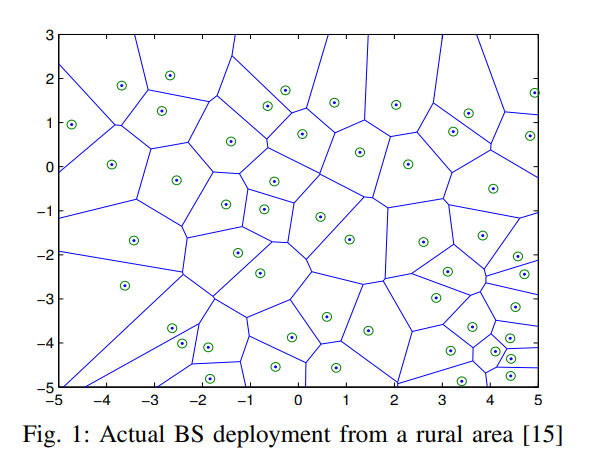
Coverage probability analysis for wireless networks using repulsive point processes
The recent witnessed evolution of cellular networks from a carefully planned deployment to more irregular, heterogeneous deployments of Macro, Pico and Femto-BSs motivates new analysis and design approaches. In this paper, we analyze the coverage probability in cellular networks assuming repulsive point processes for the base station deployment. In particular, we characterize, analytically using stochastic geometry, the downlink probability of coverage under a Matern hardcore point process to ensure minimum distance between the randomly located base stations. Assuming a mobile user connects to
Pagination
- Previous page ‹‹
- Page 10
- Next page ››
