Breadcrumb
On the secrecy capacity of fading channels
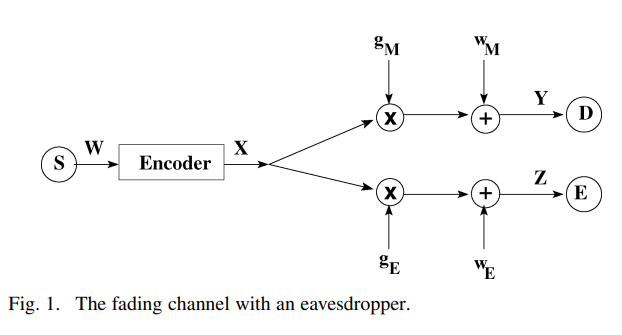
We consider the secure transmission of information over an ergodic fading channel in the presence of an eavesdropper. Our eavesdropper can be viewed as the wireless counterpart of Wyner's wiretapper. The secrecy capacity of such a system is characterized under the assumption of asymptotically long coherence intervals. We first consider the full channel state information (CSI) case, where the transmitter has access to the channel gains of the legitimate receiver and the eavesdropper. The secrecy capacity under this full CSI assumption serves as an upper bound for the secrecy capacity when only
The wiretap channel with feedback: Encryption over the channel
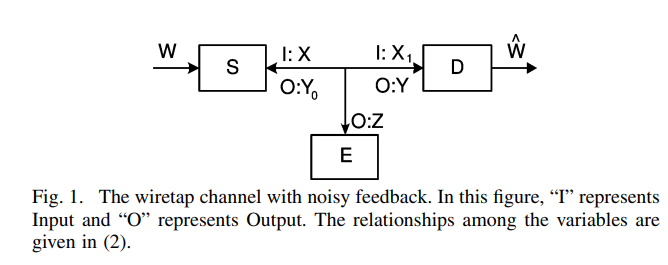
In this work, the critical role of noisy feedback in enhancing the secrecy capacity of the wiretap channel is established. Unlike previous works, where a noiseless public discussion channel is used for feedback, the feed-forward and feedback signals share the same noisy channel in the present model. Quite interestingly, this noisy feedback model is shown to be more advantageous in the current setting. More specifically, the discrete memoryless modulo-additive channel with a full-duplex destination node is considered first, and it is shown that the judicious use of feedback increases the
On the secrecy rate region for the interference channel
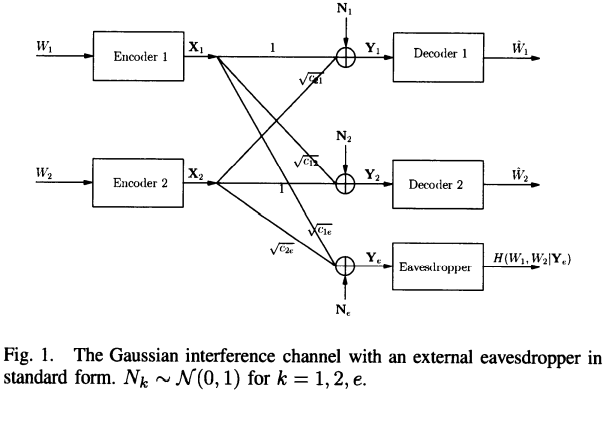
This paper studies interference channels with security constraints. The existence of an external eavesdropper in a two-user interference channel is assumed, where the network users would like to secure their messages from the external eavesdropper. The cooperative binning and channel prefixing scheme is proposed for this system model which allows users to cooperatively add randomness to the channel in order to degrade the observations of the external eavesdropper. This scheme allows users to add randomness to the channel in two ways: 1) Users cooperate in their design of the binning codebooks
Distributed flooding-based storage algorithms for large-scale wireless sensor networks
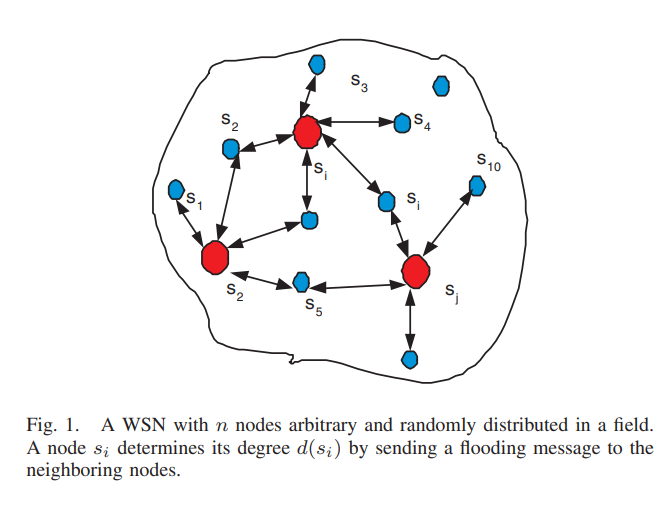
In this paper we propose distributed storage algorithms for large-scale wireless sensor networks. Assume a wireless sensor network with n nodes that have limited power, memory, and bandwidth. Each node is capable of both sensing and storing data. Such sensor nodes might disappear from the network due to failures or battery depletion. Hence it is desired to design efficient schemes to collect data from these n nodes. We propose two distributed storage algorithms (DSA's) that utilize network flooding to solve this problem. In the first algorithm, DSA-I, we assume that the total number of sensors
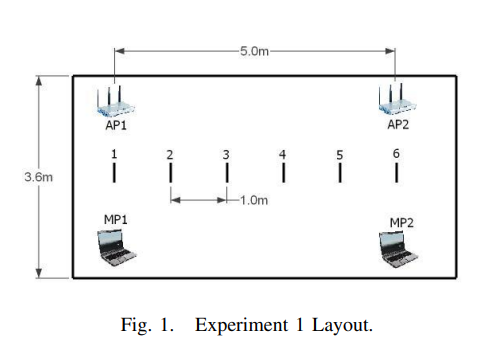
Analysis of a device-free passive tracking system in typical wireless environments
Device-free Passive (DfP) localization is a new concept in location determination where the tracked entity does not carry any device nor participate actively in the localization process. A DfP system operates by processing the received physical signal of a wireless transmitter at one or more monitoring points. The previously introduced DfP system was shown to enable the tracking of a single intruder with high accuracy in a highly controlled WLAN environment. In this paper, we propose and analyze different algorithms for DfP tracking in a typical indoor WLAN environment, rich in multipath. We
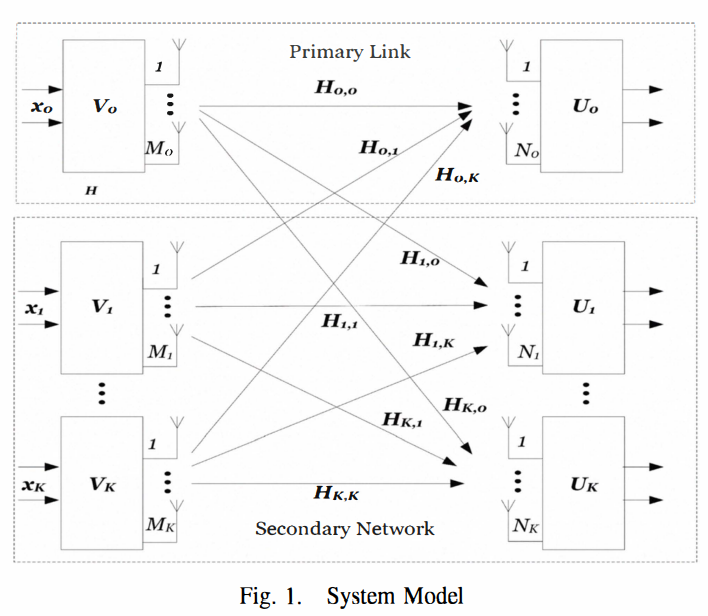
Opportunistic interference alignment for multiuser cognitive radio
We present an interference alignment (IA) technique that allows multiple opportunistic transmitters (secondary users) to use the same frequency band of a pre-existing primary link without generating any interference. The primary and secondary transmit-receive pairs are equipped with multiple antennas. We exploit the fact that under power constraints on the primary transmitter, the rate of the primary user is maximized by water-filling on the singular values of its channel matrix leaving some eigen modes unused. The secondary users can align their transmitted signals to produce a number of
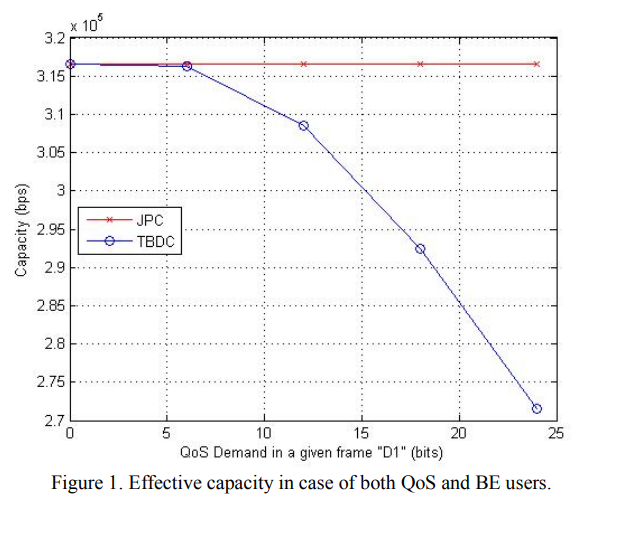
Time-based demand-constrained cross-layer resource allocation for wireless networks
Efficient resource allocation is a critical component in multi-user QoS communications and high speed networks. In this paper, we devise a new mathematical model for the resource allocation problem that takes into account the users' demands in a PHY-MAC cross-layer approach. Incorporating the time axis in our model, the target is to maximize the number of bits transmitted in a given frame rather than maximizing the channel capacity or the average throughput. Our design is governed by constraints on users' demands (expressed in bits), energy expenditure, and frame duration. We model the
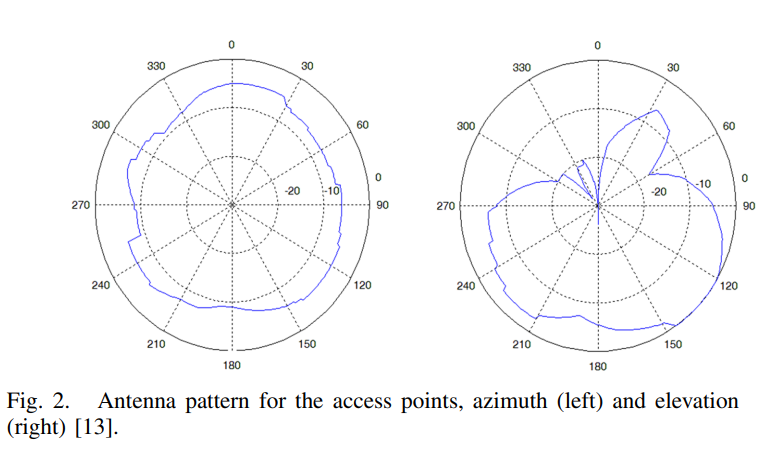
Propagation modeling for accurate indoor WLAN RSS-based localization
WLAN RSS-based localization has been a hot research topic for the last years. To obtain high accuracy in the noisy wireless channel, WLAN location determination systems usually use a calibration phase, where a radio map, capturing the signal strength signatures at different locations in the area of interest, is built. The radio map construction process takes a lot of time and effort, reducing the value of WLAN localization systems. In this paper, we propose 3D ray tracing as a way for automatically generating a highly accurate radiomap. We compare this method to previously used propagation
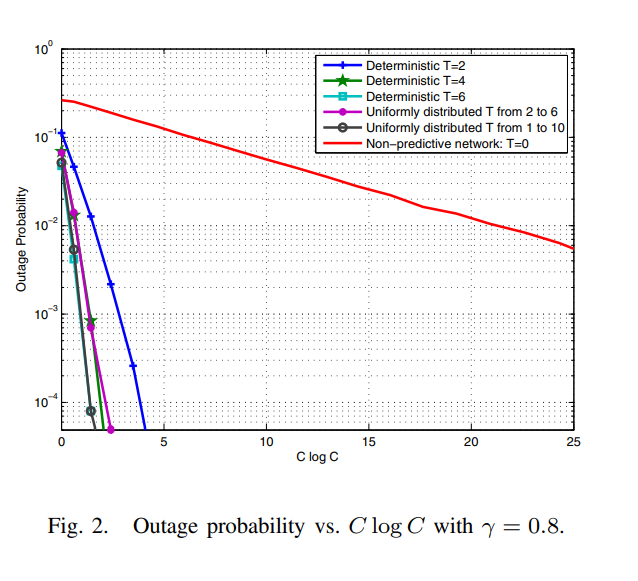
Proactive resource allocation: Turning predictable behavior into spectral gain
This paper introduces the novel concept of proactive resource allocation in which the predictability of user behavior is exploited to balance the wireless traffic over time, and hence, significantly reduce the bandwidth required to achieve a given blocking/outage probability. We start with a simple model in which the smart wireless devices are assumed to predict the arrival of new requests and submit them to the network T time slots in advance. Using tools from large deviation theory, we quantify the resulting prediction diversity gain to establish that the decay rate of the outage event
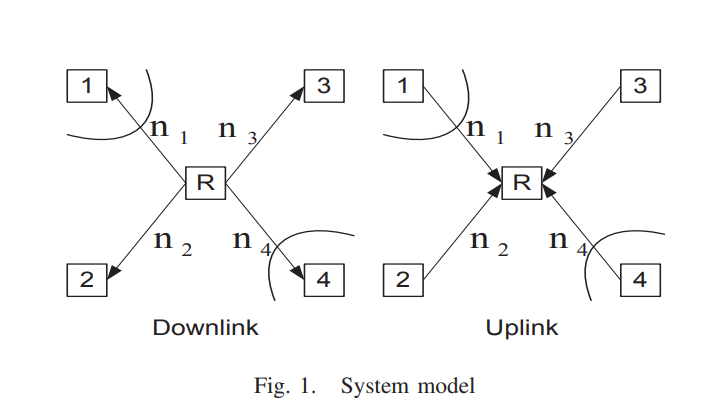
On the deterministic multicast capacity of bidirectional relay networks
In this paper, we completely characterize the deterministic multicast capacity region of the symmetric two-pair bidirectional half duplex relay network with private messages. Towards this end, we first develop a new upper bound on the deterministic capacity region, based on the notion of a one-sided genie. We then proceed to construct novel detour schemes that achieve the upper bound by routing the bits intended for a certain receiver through the network rather than sending it directly. To the best of the authors' knowledge, this scenario corresponds to one of the rare cases where coding
Pagination
- Previous page ‹‹
- Page 7
- Next page ››
