Breadcrumb
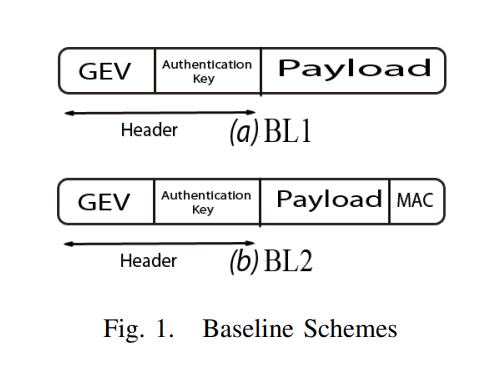
SANC: Source authentication using network coding
In this paper, we explore the security merits of network coding and potential trade-offs with the widely accepted throughput benefits, especially in multicast scenarios. In particular, we propose a novel Source Authentication using Network Coding (SANC) scheme that can either complement state-of-the-art application-layer authentication schemes proposed in the literature or be used as a stand-alone scheme in network coding-based networks. Towards this objective, we propose a general framework for embedding the authentication information within the network coding Global Encoding Vector. This is
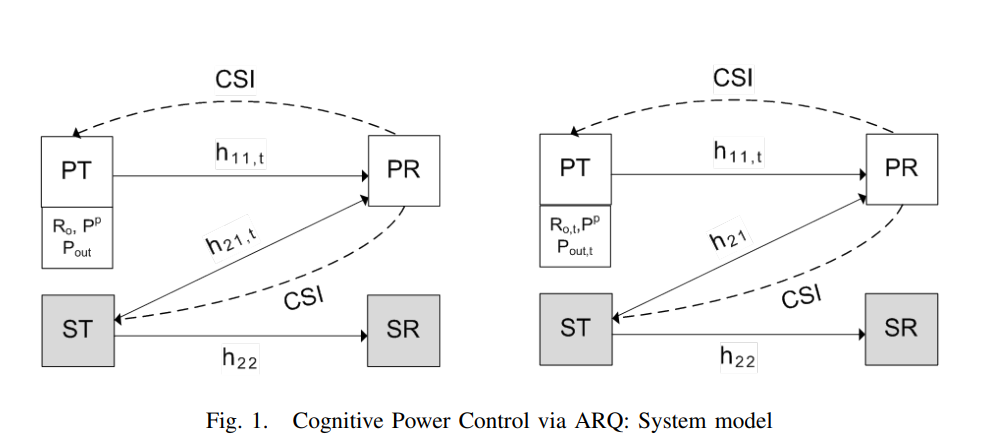
Throughput maximization over temporally correlated fading channels in cognitive radio networks
We consider a primary link and a secondary link, each composed of a transmitter and a receiver. The primary channel and the channel between the secondary transmitter and the primary receiver follow a first-order Markov model for channel variation over time. Under this assumption of temporal correlation and via exploiting the channel state information (CSI) feedback, we pose the cognitive power control problem as the maximization of secondary throughput subject to a constraint on the primary outage. To solve this problem, we assume that the primary transmitter sends with a constant-rate and
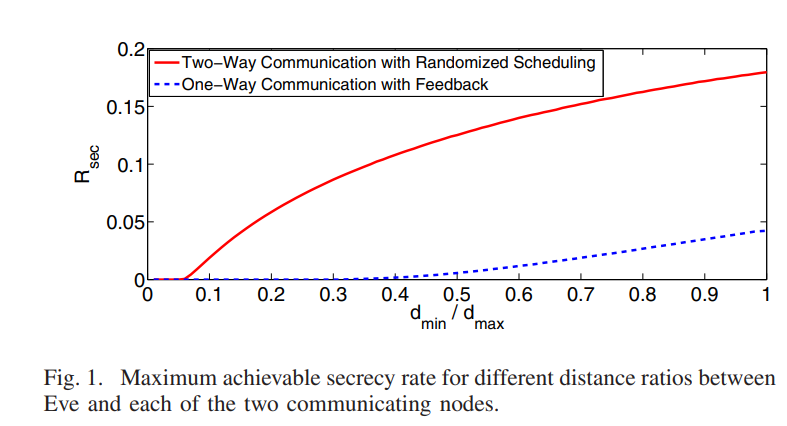
Randomization for security in half-duplex two-way Gaussian channels
This paper develops a new physical layer framework for secure two-way wireless communication in the presence of a passive eavesdropper, i.e., Eve. Our approach achieves perfect information theoretic secrecy via a novel randomized scheduling and power allocation scheme. The key idea is to allow Alice and. Bob to send symbols at random time instants. While Alice will be able to determine the symbols transmitted by Bob, Eve will suffer from ambiguity regarding the source of any particular symbol. This desirable ambiguity is enhanced, in our approach, by randomizing the transmit power level. Our
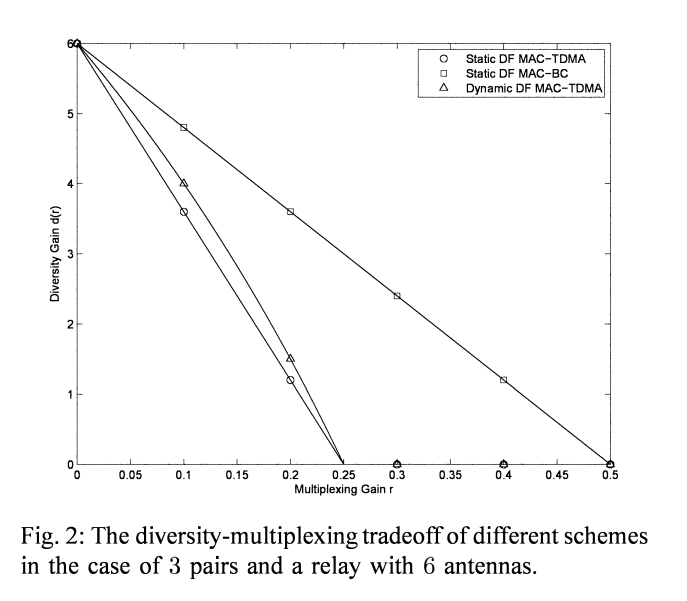
The MIMO wireless switch: Relaying can increase the multiplexing gain
This paper considers an interference network composed of K half-duplex single-antenna pairs of users who wish to establish bi-directional communication with the aid of a multiinput-multi-output (MIMO) half-duplex relay node. This channel is referred to as the "MIMO Wireless Switch" since, for the sake of simplicity, our model assumes no direct link between the two end nodes of each pair implying that all communication must go through the relay node (i.e., the MIMO switch). Assuming a delay-limited scenario, the fundamental limits in the high signal-to-noise ratio (SNR) regime is analyzed using
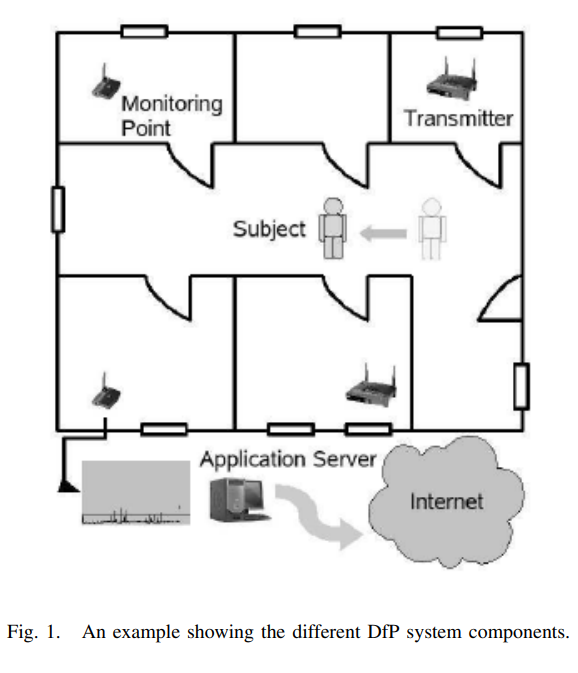
Smart devices for smart environments: Device-free passive detection in real environments
Device-free Passive (DfP) localization is a system envisioned to detect, track, and identify entities that do not carry any device, nor participate actively in the localization process. A DfP system allows using nominal WiFi equipment for intrusion detection, without using any extra hardware, adding smartness to any WiFi-enabled device. In this paper, we focus on the detection function of the DfP system in a real environment. We show that the performance of our previously developed algorithms for detection in a controlled environments, which achieved 100% recall and precision, degrades
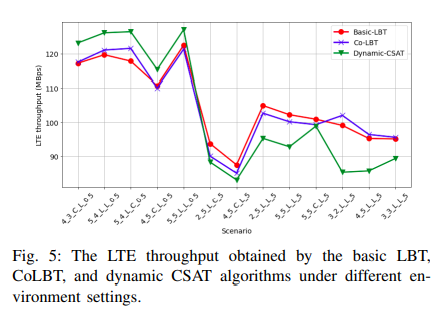
Machine Learning-based Module for Monitoring LTE/WiFi Coexistence Networks Dynamics
Long-Term Evolution (LTE) technology is expected to shift some of its transmissions into the unlicensed band to overcome the spectrum scarcity problem. Nevertheless, in order to effectively use the unlicensed spectrum, several challenges have to be addressed. The most important of which is how to coexist with the incumbent unlicensed WiFi networks. Incorporating the "intelligence"component into the network radios is foreseen to resolve the intrinsic network challenges, rather than conventional non-adaptive action plans. Specifically, an intelligent cognitive engine (CE) that continuously

Early breast cancer diagnostics based on hierarchical machine learning classification for mammography images
Breast cancer constitutes a significant threat to women’s health and is considered the second leading cause of their death. Breast cancer is a result of abnormal behavior in the functionality of the normal breast cells. Therefore, breast cells tend to grow uncontrollably, forming a tumor that can be felt like a breast lump. Early diagnosis of breast cancer is proved to reduce the risks of death by providing a better chance of identifying a suitable treatment. Machine learning and artificial intelligence play a key role in healthcare systems by assisting physicians in diagnosing early, better
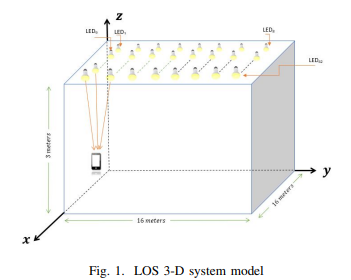
Visible Light Communications Localization Error Enhancement using Parameter Relaxation
In this paper, we propose applying a parameter relaxation technique to the location estimation algorithm that is based on the Received Signal Strength (RSS) of Visible Light Communications (VLC). A hybrid system of localization balancing is introduced, where the localization algorithm is developed with and without this efficient parameter relaxation. The results show that applying the parameter relaxation reduces the localization Root Mean Square (RMS) error by 43% of that without relaxation; and the processing time is reduced by 18% of that without relaxation. Moreover, the parameter
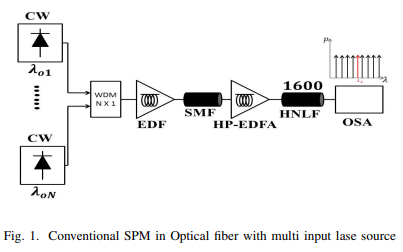
Generation of OFC by Self-Phase Modulation and Multiple Laser Sources in HNLF
Self-Phase Modulation (SPM) is a non-linear phenomenon relating to the self-induced phase shift encountered by the optical field during its transmission into the optical fiber. It is the most popular technique for generating an optical frequency comb (OFC) with different frequency spacing values. The SPM is regulated by many parameters such as fiber length, input optical power, and the non-linearity of the optical fiber. The OFC distinguishes between a high spectral flatness level, a high optical signal-to-noise ratio (OSNR) and a wide range of wavelengths. In this paper, The SPM uses to
Generic evaluation of FSO system over Málaga turbulence channel with MPPM and non-zero-boresight pointing errors
Free space optical (FSO) communication channels are affected by fluctuations in irradiance due to atmospheric turbulence and pointing errors. Recently, a generalized statistical model knows as Málaga (M) was developed to describe irradiance fluctuations of the beam propagating through a turbulent medium. In this paper, an approximate finite-series probability density function (PDF) for composite M turbulence with pointing errors is verified. Considering multiple pulseposition- modulation (MPPM) with intensity modulation and direct detection, specific closed-form expressions for average symbol
Pagination
- Previous page ‹‹
- Page 6
- Next page ››
