Breadcrumb
6G: A comprehensive survey on technologies, applications, challenges, and research problems
The inherent limitations of the network keep on going to be revealed with the continuous deployment of cellular networks. The next generation 6G is motivated by these drawbacks to properly integrate important rate-hungry applications such as extended reality, wireless brain-computer interactions, autonomous vehicles, and so on. Also, to support significant applications, 6G will handle large amounts of data transmission in smart cities with much lower latency. It combines many state-of-the-art trends and technology to provide higher data rates for ultra-reliable and low latency communications
Demonstration of Forward Collision Warning System Based on Real-Time Computer Vision
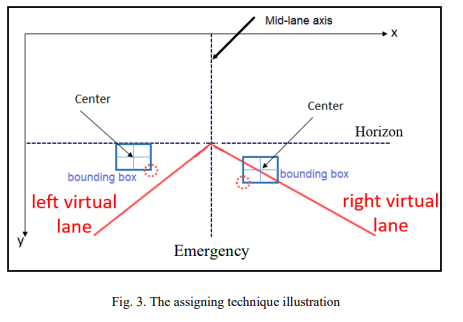
This paper demonstrates the software and hardware of a forward-collision warning system using techniques of realtime computer vision which helps self-driving cars and autonomous vehicles systems to merge with the road environment safely and ensure the reliability of these systems. The software approach of the paper consists of five parts: car detection, depth estimation, lane assignation, the relative speed of other cars and their corresponding speed limit and finally ultrasonic sensors which completes the front of the vehicle as the camera can't cover it alone. Besides these five objectives
Dynamic Traffic Model with Optimal Gateways Placement in IP Cloud Heterogeneous CRAN
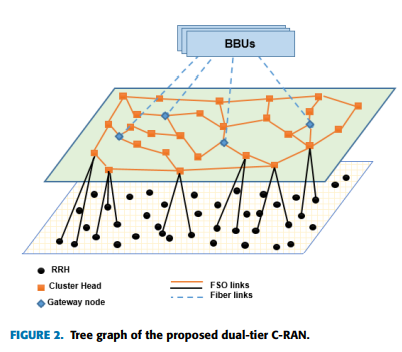
In this paper, topology design, optimal routing, and gateways placement selection algorithms are proposed in Heterogeneous Cloud Radio Access Network (C-RAN) with exploiting Free Space Optical (FSO) communication. The proposed network consists of two tiers; the lower tier concerns with clustering Remote Radio Heads (RRHs) based on traffic demands. The upper tier consists of transceivers along with the Cluster Heads (CHs) and gateways. Algorithms are proposed to achieve the lowest number of edges and the highest possible throughput based on the presented optimization problem. Moreover, route
Review organic solar cells parameters extraction and characterization techniques
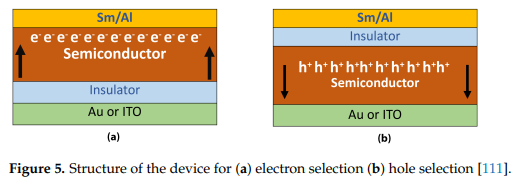
Organic photovoltaic research is continuing in order to improve the efficiency and stability of the products. Organic devices have recently demonstrated excellent efficiency, bringing them closer to the market. Understanding the relationship between the microscopic parameters of the device and the conditions under which it is prepared and operated is essential for improving performance at the device level. This review paper emphasizes the importance of the parameter extraction stage for organic solar cell investigations by offering various device models and extraction methodologies. In order
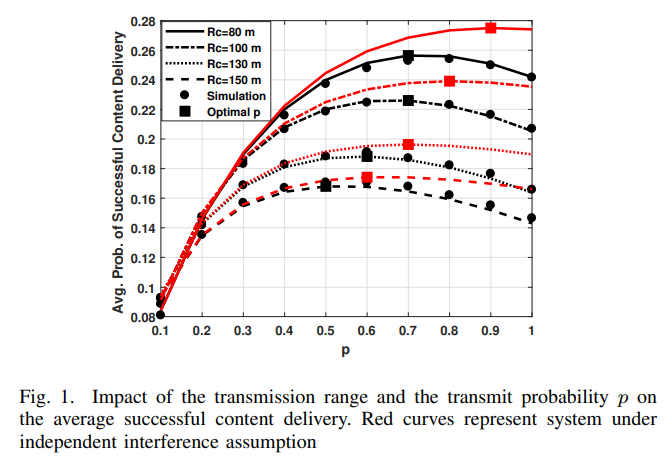
Impact of Temporally Correlated Nakagami-m Interferers in D2D Cache-Aided Networks
In this paper, we exploit tools from stochastic geometry to characterize the average probability of successful content delivery in a cache-enabled device-to-device (D2D) network under Nakagami- m fading. Specifically, we focus on the impact of temporal interference correlation due to erroneous packets retransmissions. The aggregate network interference is characterized under a slotted Aloha scheme in a homogeneous Poisson field of static interferers. In addition, the effect of different system parameters, such as the content popularity, intensity of devices, and D2D communication range, on the

Transmit and receive cooperative cognition: Protocol design and stability analysis
In this paper, we investigate the stability of a cooperative cognitive system. We propose a cooperative secondary transmitter-receiver system (CSTR), where, the secondary transmitter (ST) and the secondary receiver (SR) increase the spectrum availability for the ST packets by relaying the unsuccessfully transmitted packets of the primary transmitter (PT). We assume receiving nodes with multipacket reception capability (MPR). We provide two inner bounds and two outer bounds on the stability region of the considered system. © 2013 ICST - The Institute for Computer Sciences, Social Informatics
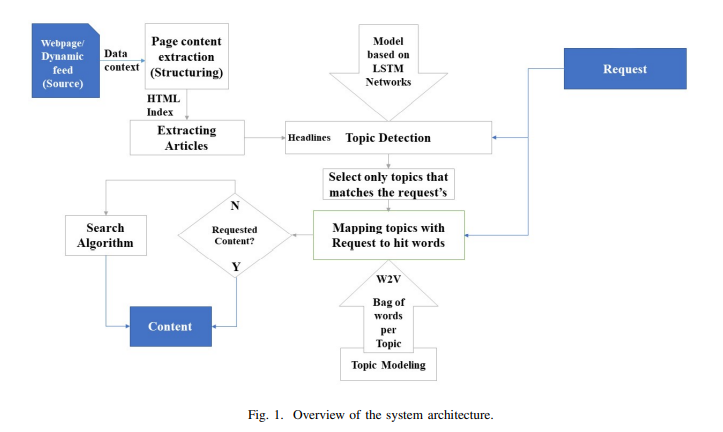
Towards Intelligent Web Context-Based Content On-Demand Extraction Using Deep Learning
Information extraction and reasoning from massive high-dimensional data at dynamic contexts, is very demanding and yet is very hard to obtain in real-time basis. However, such process capability and efficiency might be affected and limited by the available computational resources and the consequent power consumption. Conventional search mechanisms are often incapable of real-time fetching a predefined content from data source, without concerning the increased number of connected devices that contribute to the same source. In this work, we propose and present a concept for an efficient approach
Optimum Scheduling of the Disinfection Process for COVID-19 in Public Places with a Case Study from Egypt, a Novel Discrete Binary Gaining-Sharing Knowledge-Based Metaheuristic Algorithm
The aim of this paper is to introduce an improved strategy for controlling COVID-19 and other pandemic episodes as an environmental disinfection culture for public places. The scheduling aims at achieving the best utilization of the available working day-time hours, which is calculated as the total consumed disinfection times minus the total loosed transportation times. The proposed problem in network optimization identifies a disinfection group who is likely to select a route to reach a subset of predetermined public places to be regularly disinfected with the most utilization of the
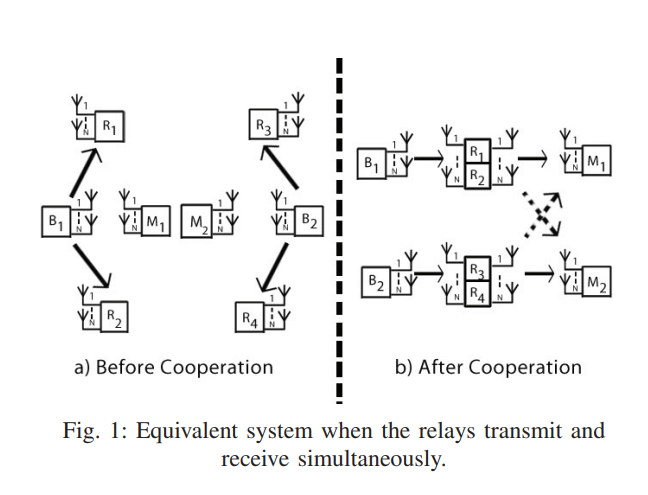
Alternate relaying and the degrees of freedom of one-way cellular relay networks
In this paper, a cellular relaying network consisting of two source-destination pairs, and four decode-and-forward relays operating in half-duplex mode is considered. Each source is assisted by two relays and all nodes are equipped with N antennas. In order to compensate for the loss of capacity by a factor of half due to the half-duplex mode, an alternate transmission protocol among the two relays is proposed. An outer bound on the degrees of freedom (DoF) of this system is developed. A constructive proof of achievability based on two different schemes is provided. Aligning the inter-relay
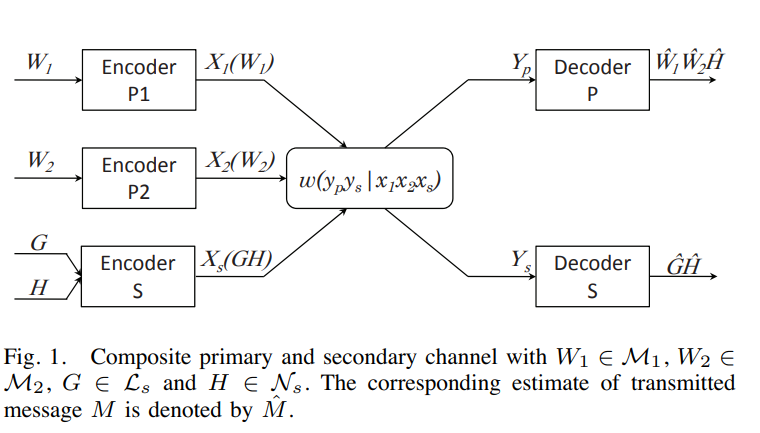
An achievable rate region for a primary network shared by a secondary link
We consider a multiple access primary network with N transmitters. A secondary link of one transmitter and a corresponding receiver causes interference to the primary network. An achievable rate region for the primary network and the secondary link is obtained given the following mode of operation. The secondary transmitter employs rate-splitting so that the primary receiver can decode part of the secondary's signal and cancel it. The secondary receiver, on the other hand, treats primary interference as noise. Given a Gaussian channel model, we investigate the effect of rate-splitting on the
Pagination
- Previous page ‹‹
- Page 28
- Next page ››
