Breadcrumb
Blind cognitive MAC protocols
We consider the design of cognitive Medium Access Control (MAC) protocols enabling an unlicensed (secondary) transmitter-receiver pair to communicate over the idle periods of a set of licensed channels, i.e., the primary network. The objective is to maximize data throughput while maintaining the synchronization between secondary users and avoiding interference with licensed (primary) users. No statistical information about the primary traffic is assumed to be available a-priori to the secondary user. We investigate two distinct sensing scenarios. In the first, the secondary transmitter is
Formal specification and analysis of the PCF protocol in the 802.11 standard using systems of communicating machines
With the widespread usage of the 802.11 protocol, it becomes important to study the protocol operation. In this paper we propose a formal model for the point coordination function (PCF) of the 802.11 MAC layer using systems of communicating machines. Our goal is to analyse the protocol for safety and liveness properties. These properties cannot be verified directly from the protocol description. Analysis shows that the PCF protocol is free from deadlocks and non-executable transitions. We also show that liveness is guaranteed in the PCF protocol.
Cooperation and underlay mode selection in cognitive radio network
In this paper, we propose a technique for cooperation and underlay mode selection in cognitive radio networks. Hybrid spectrum sharing is assumed where the secondary user (SU) can access the primary user (PU) channel in two modes, underlay mode or cooperative mode with admission control. Overlay spectrum sharing allows the SU to occupy the spectrum only when the PU is idle. Cooperation (collaboration) occurs when the SU admits the PU's packet into a relay buffer to transmit in the subsequent timeslots, i.e. timeslots when no successful transmission from the PU source to the destination. In
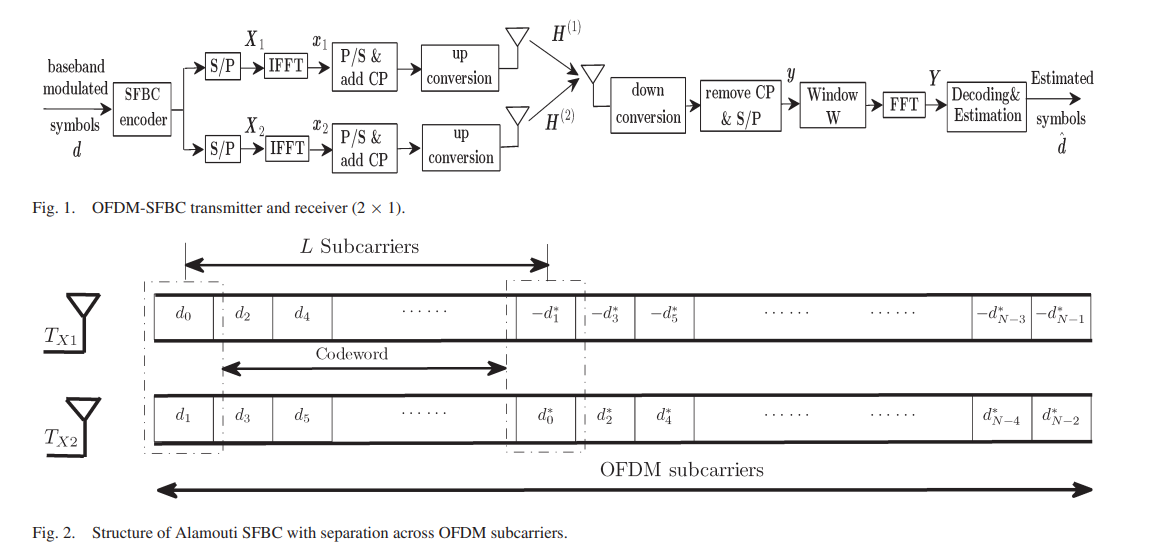
Optimal windowing and decision feedback equalization for space-frequency alamouti-coded OFDM in doubly selective channels
Space-frequency block coding with orthogonal frequency-division multiplexing (SFBC-OFDM) suffers from the effect of intercarrier interference (ICI) in doubly selective channels. In this paper, a scheme is proposed in which windowing is applied to the received signal to reduce the effect of ICI to a limited number of neighboring subcarriers. The subcarriers holding the SFBC components of each codeword are separated by a number of subcarriers larger than the ICI range, and hence, they do not interfere with each other. To preserve the structure of the SFBC, the separation between the codeword
Cache-Aware Source Coding
In this letter, we show that Huffman's source coding method is not optimal for cache-aided networks. To that end, we propose an optimal algorithm for the cache-aided source coding problem. We define cache-aided entropy, which represents a lower bound on the average number of transmitted bits for cached-aided networks. A sub-optimal low-complexity cache-aided coding algorithm is presented. In addition, we propose a novel polynomial-time algorithm that obtains the global-optimal source code for wide range of cache sizes. Simulation results show a reduction in the average number of transmitted
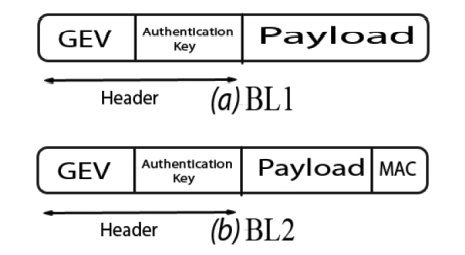
A source authentication scheme using network coding
In this paper, we explore the security merits of network coding and potential trade-offs with the widely accepted throughput benefits, especially in multicast scenarios. In particular, we propose a novel Source Authentication using Network Coding (SANC) scheme. Towards this objective, we propose a general framework for embedding the authentication information within the network coding Global Encoding Vector. First, we illustrate the proposed concept using a simple mapping function. Second, we present a detailed security analysis that reveals the security merits of the proposed scheme
Cognitive Radio Networks with Probabilistic Relaying: Stable Throughput and Delay Tradeoffs
This paper studies fundamental throughput and delay tradeoffs in cognitive radio systems with cooperative secondary users. We focus on randomized cooperative policies, whereby the secondary user (SU) serves either its own queue or the primary users (PU) relayed packets queue with certain service probability. The proposed policy opens room for trading the PU delay for enhanced SU delay, and vice versa, depending on the application QoS requirements. Towards this objective, the system's stable throughput region is characterized. Furthermore, the moment generating function approach is employed and
Cooperative access in cognitive radio networks: Stable throughput and delay tradeoffs
In this paper, we study and analyze fundamental throughput-delay tradeoffs in cooperative multiple access for cognitive radio systems. We focus on the class of randomized cooperative policies, whereby the secondary user (SU) serves either the queue of its own data or the queue of the primary user (PU) relayed data with certain service probabilities. The proposed policy opens room for trading the PU delay for enhanced SU delay. Towards this objective, stability conditions for the queues involved in the system are derived. Furthermore, a moment generating function approach is employed to derive
Fingerprinting with minimum distance decoding
This paper adopts an information-theoretic framework for the design of collusion-resistant coding/decoding schemes for digital fingerprinting. More specifically, the minimum distance decision rule is used to identify 1 out of $t$ pirates. Achievable rates, under this detection rule, are characterized in two scenarios. First, we consider the averaging attack where a random coding argument is used to show that the rate 1/2 is achievable with $t=2$ pirates. Our study is then extended to the general case of arbitrary $t$ highlighting the underlying complexity-performance tradeoff. Overall, these
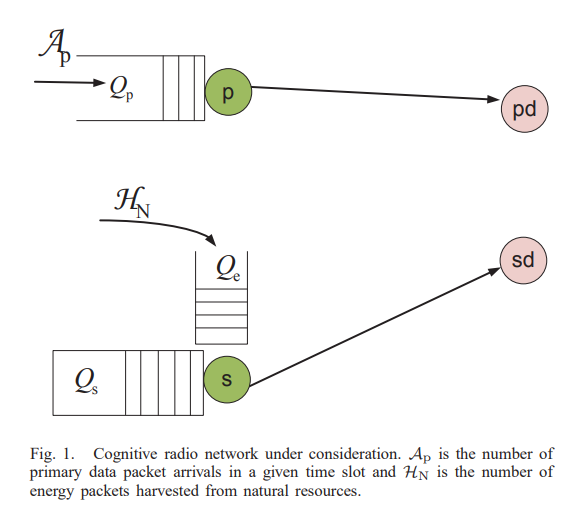
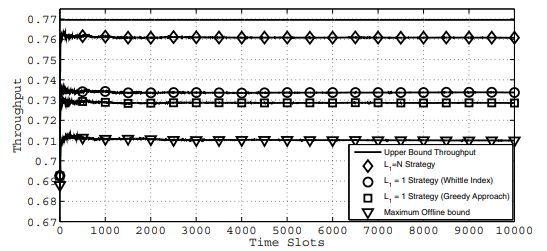
Optimal spectrum access for a rechargeable cognitive radio user based on energy buffer state
This paper investigates the maximum throughput for a rechargeable secondary user (SU) sharing the spectrum with a primary user (PU) plugged to a reliable power supply. The SU maintains a finite energy queue and harvests energy from natural resources, e.g., solar, wind and acoustic noise. We propose a probabilistic access strategy by the SU based on the number of packets at its energy queue. In particular, when the energy queue is in a certain state, the SU probabilistically uses a total number of energy packets that is at most equal to the number of packets at its energy queue. The probability
Pagination
- Previous page ‹‹
- Page 26
- Next page ››

