Breadcrumb
Fractional sequential sensing for energy efficient cooperative cognitive radio networks
In this paper, we propose fractional sequential sensing (FSS) as a novel cooperative sensing scheme for cognitive radio networks. FSS compromises a tradeoff between sensing accuracy and efficiency by formulating an optimization problem whose solution identifies FSS sensing parameters. These parameters include the sensing period and channels allocated for each user. Our simulation results show that FSS successfully improves the sensing accuracy while maintaining a low power profile. Additionally, we show that the sensing accuracy performance gap between FSS and other traditional schemes
Cognitive radio transmission strategies for primary erasure channels
A fundamental problem in cognitive radio systems is that the secondary user is ignorant of the primary channel state and the interference it inflicts on the primary license holder. We consider a secondary user that can eavesdrop on the ACK/NACK Automatic Repeat reQuest (ARQ) fed back from the primary receiver to the primary transmitter. Assuming the primary channel states follow a Markov chain, this feedback gives the secondary user an indication of the primary channel quality. Based on the ACK/NACK received, we devise optimal transmission strategies for the secondary user so as to maximize a
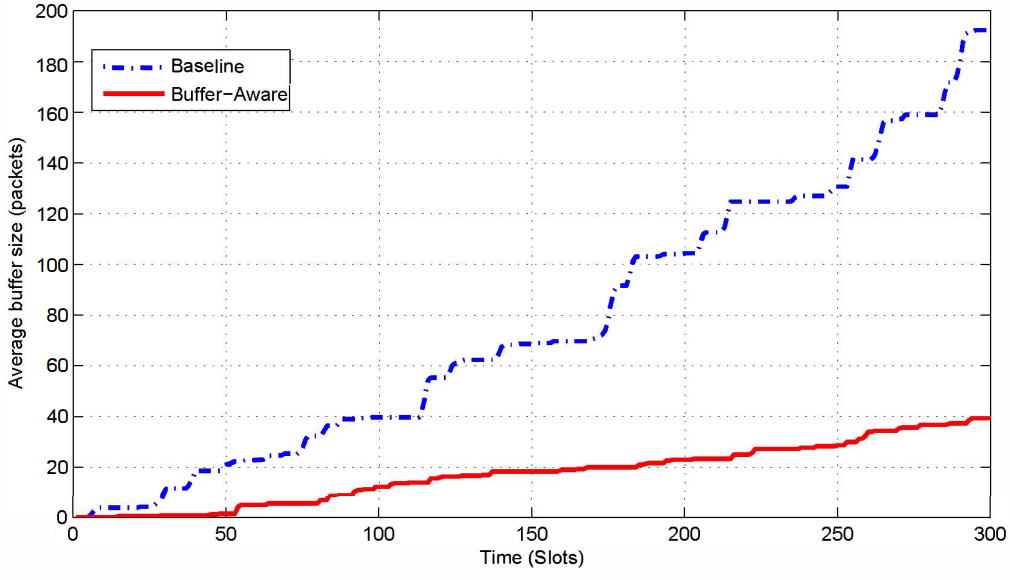
Buffer-aware power control for cognitive radio networks
In this paper we study the problem of buffer-aware power control in underlay cognitive radio networks. In particular, we investigate the role of buffer state information, manifested through the secondary users' queue lengths, along with channel state information in the cognitive radio power control problem. Towards this objective, we formulate a constrained optimization problem to find the set of secondary user transmit powers that maximizes the sum of rates weighted by the respective buffer lengths subject to signal-to- interference-and-noise-ratio (SINR) and maximum power constraints

A soft sensing-based cognitive access scheme exploiting primary feedback
In this paper, we examine a cognitive spectrum access scheme in which secondary users exploit the primary feedback information. We consider an overlay secondary network employing a random access scheme in which secondary users access the channel by certain access probabilities that are function of the spectrum sensing metric. In setting our problem, we assume that secondary users can eavesdrop on the primary link's feedback. We study the cognitive radio network from a queuing theory point of view. Access probabilities are determined by solving a secondary throughput maximization problem
Censoring for improved performance of distributed detection in wireless sensor networks
In this paper, we consider the problem of binary hypothesis testing for distributed detection in wireless sensor networks in which a transmission censoring scheme is employed. The sensor nodes transmit binary decisions to the fusion center (FC) for final decision making. Sensor nodes with unreliable observation samples censor transmission to FC. By having two thresholds at each sensor node, a sensor node censors transmission if its log-likelihood ratio (LLR) falls between the two thresholds, whereas the more informative sensor nodes transmit their decisions to the FC. In this case of censoring
A hidden Markov model for localization using low-end GSM cell phones
Research in location determination for GSM phones has gained interest recently as it enables a wide set of location based services. RSSI-based techniques have been the preferred method for GSM localization on the handset as RSSI information is available in all cell phones. Although the GSM standard allows for a cell phone to receive signal strength information from up to seven cell towers, many of today's cell phones are low-end phones, with limited API support, that gives only information about the associated cell tower. In addition, in many places in the world, the density of cell towers is
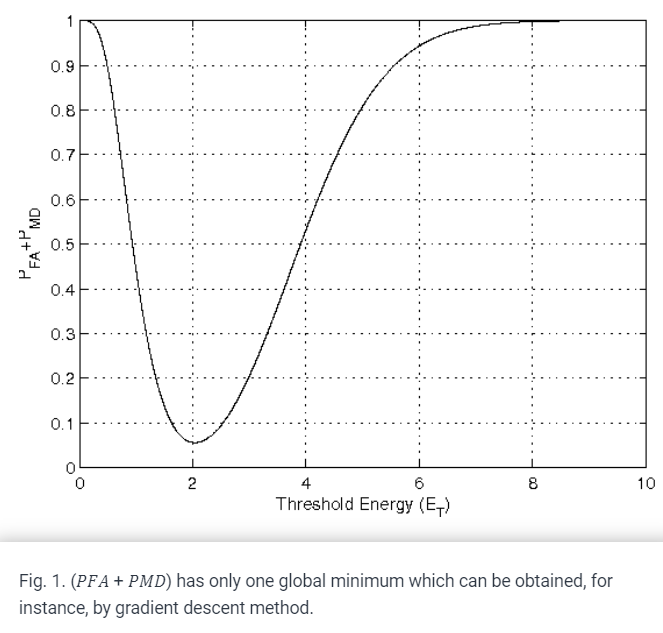
Optimization of channel sensing time and order for cognitive radios
In this paper we consider a single cognitive radio seeking a transmission opportunity by sequentially sensing a number of statistically independent primary channels. We study the joint optimization of the time spent to sense a channel, the decision threshold to determine whether the channel is free or busy, together with the order with which the channels are sensed. The sensing time and decision threshold are assumed to be the same for all channels. The design objective is to maximize the expected secondary throughput taking sensing errors into account and penalizing for collisions that may
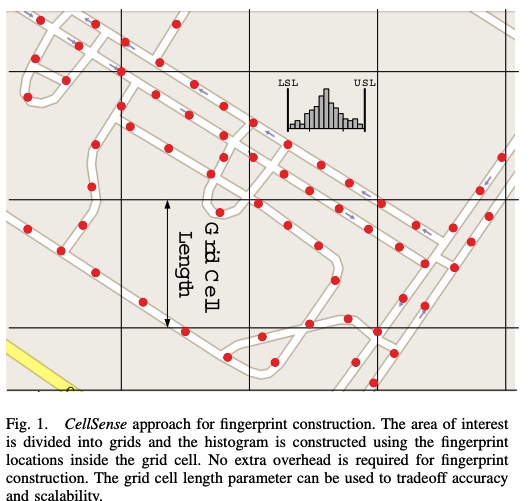
CellSense: A probabilistic RSSI-based GSM positioning system
Context-aware applications have been gaining huge interest in the last few years. With cell phones becoming ubiquitous computing devices, cell phone localization has become an important research problem. In this paper, we present CellSense, a probabilistic RSSI-based fingerprinting location determination system for GSM phones.We discuss the challenges of implementing a probabilistic fingerprinting localization technique in GSM networks and present the details of the CellSense system and how it addresses the challenges. To evaluate our proposed system, we implemented CellSense on Android-based
Hidden anchor: A lightweight approach for physical layer location privacy
In hybrid wireless sensor networks, where trusted and un-trusted nodes coexist, it becomes important to allow trusted nodes to share information, especially, location information and prevent un-trusted nodes from gaining access to this information. We focus on anchor-based localization algorithms in WSNs, where a small set of specialized nodes, that is, anchor nodes, broadcast their location to the network and other nodes can use the broadcast information to estimate their own location. The main challenge is that both trusted and un-trusted nodes can measure the physical signal transmitted
ARQ-based secret key sharing
This paper develops a novel framework for sharing secret keys using existing Automatic Repeat reQuest (ARQ) protocols. Our approach exploits the multi-path nature of the wireless environment to hide the key from passive eavesdroppers. The proposed framework does not assume the availability of any prior channel state information (CSI) and exploits only the one bit ACK/NACK feedback from the legitimate receiver. Compared with earlier approaches, the main innovation lies in the distribution of key bits among multiple ARQ frames. Interestingly, this idea allows for achieving a positive secrecy
Pagination
- Previous page ‹‹
- Page 25
- Next page ››

