Breadcrumb
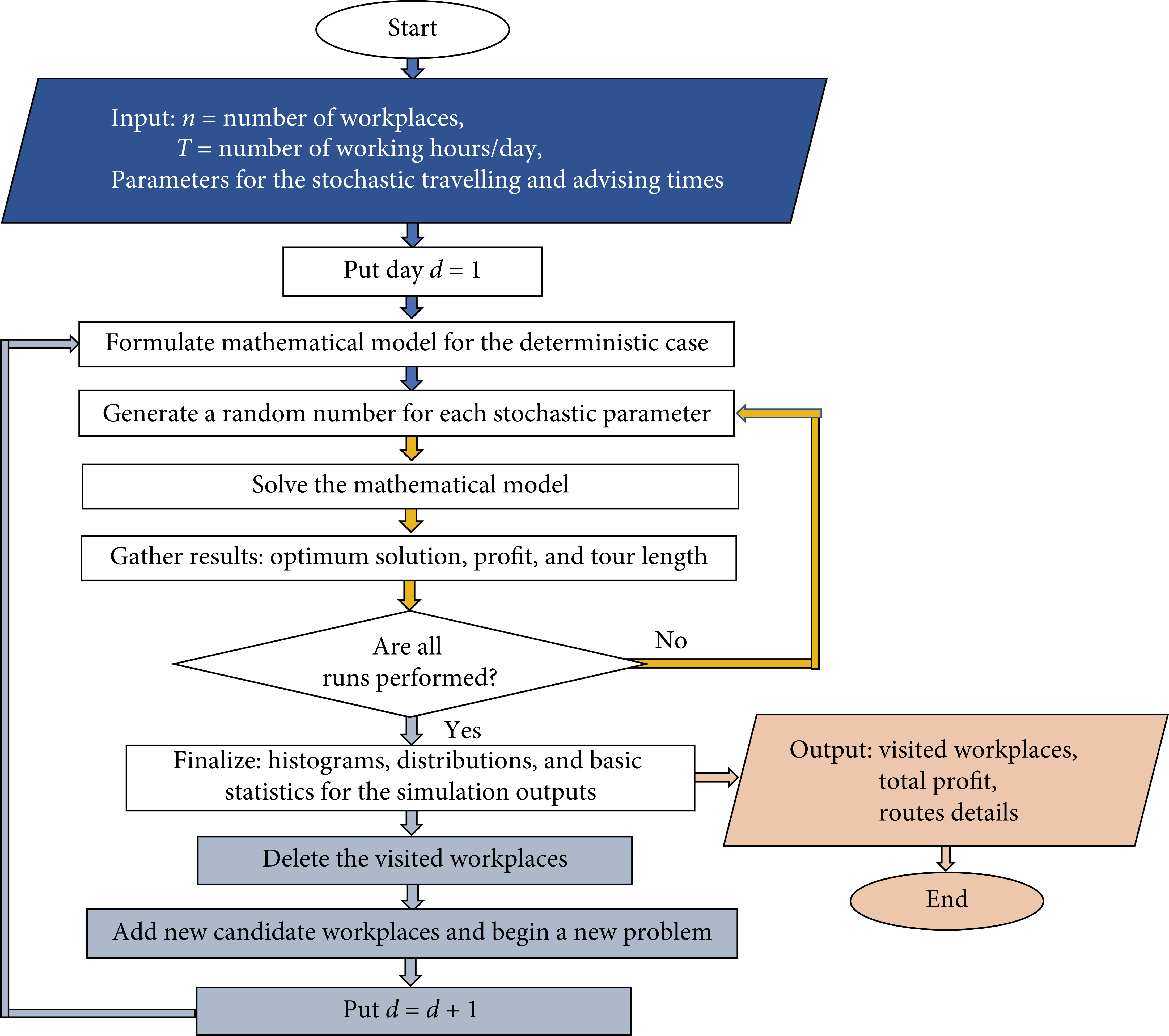
Stochastic travelling advisor problem simulation with a case study: A novel binary gaining-sharing knowledge-based optimization algorithm
Neural Knapsack: A Neural Network Based Solver for the Knapsack Problem
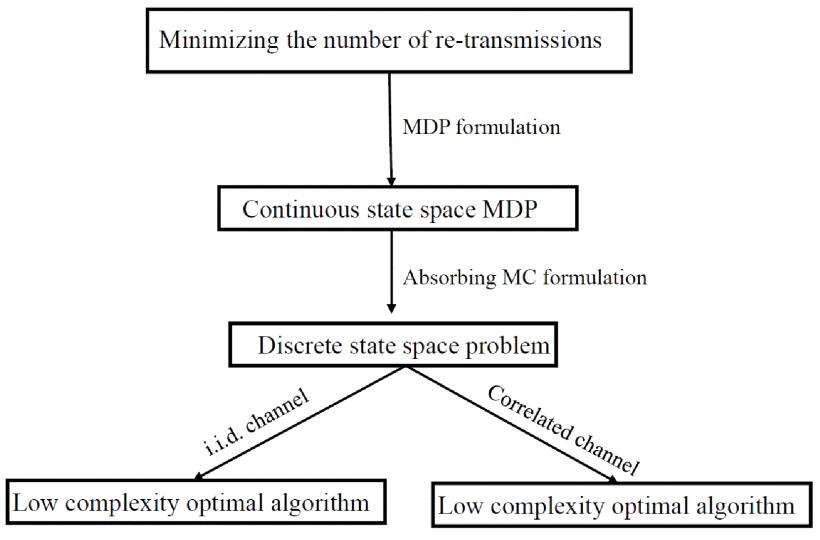
SWIPT Using Hybrid ARQ over Time Varying Channels
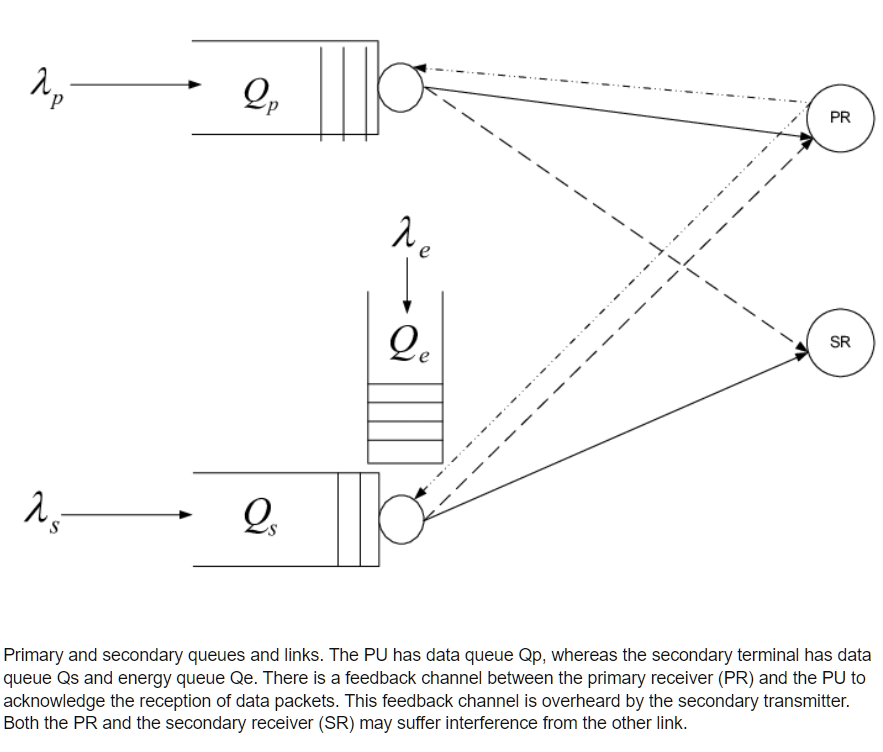
Optimal random access and random spectrum sensing for an energy harvesting cognitive radio
We consider a secondary user with energy harvesting capability. We design access schemes for the secondary user which incorporate random spectrum sensing and random access, and which make use of the primary automatic repeat request (ARQ) feedback. The sensing and access probabilities are obtained such that the secondary throughput is maximized under the constraints that both the primary and secondary queues are stable and that the primary queueing delay is kept lower than a specified value needed to guarantee a certain quality of service (QoS) for the primary user. We consider spectrum sensing

Optimal random access for a cognitive radio terminal with energy harvesting capability
The deterministic multicast capacity of 4-node relay networks
In this paper, we completely characterize the deterministic capacity region of a four-node relay network with no direct links between the nodes, where each node communicates with the three other nodes via a relay. Towards this end, we develop an upper bound on the deterministic capacity region, based on the notion of a one-sided genie. To establish achievability, we use the detour schemes that achieve the upper bound by routing specific bits via indirect paths instead of sending them directly. © 2013 IEEE.
Towards evolving sensor actor networks
Sensor Actor NETworks (SANET) represent a major component of ubiquitous service environments promising interesting solutions to a wide range of problems. Despite the obvious increase in the research activities proposing architectures and protocols for SANETs, we are still no where near the production of industrial-grade SANET software that can be relied upon for mission critical applications. The cost of programming, deploying and maintaining SANET environments is still highly prohibitive due to the lack of industrial tools capable of realizing adaptive SANET software in a cost effective way
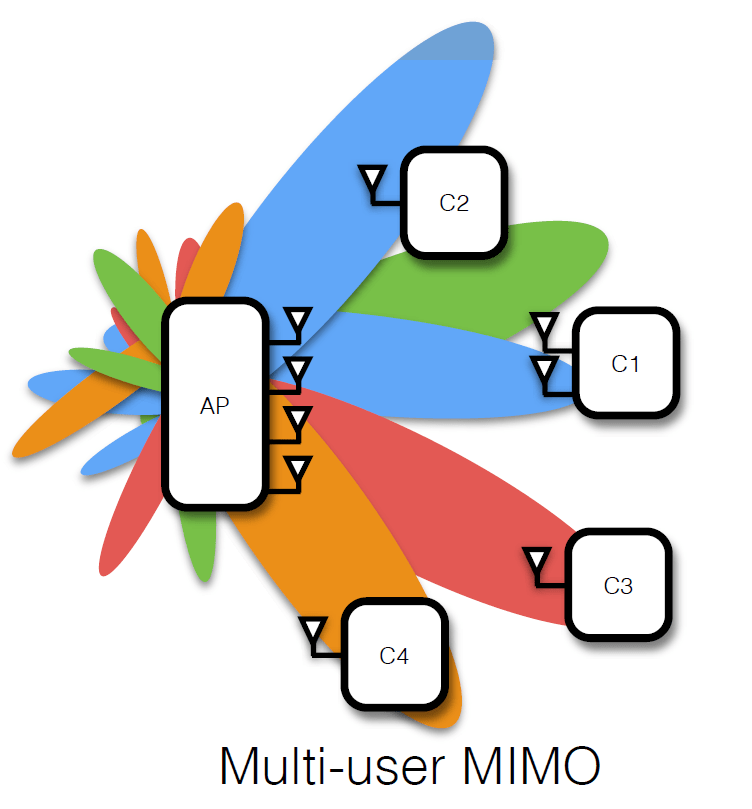
Multiuser MIMO relaying under quality of service constraints
We consider a wireless communication scenario with K source-destination pairs communicating through several half-duplex amplify-and-forward relays. We design the relay beamforming matrices by minimizing the total power transmitted from all the relays subject to quality of service constraints on the received signal to interference-plus-noise ratio at each destination node. We propose a novel method for solving the resulting nonconvex optimization problem in which the problem is decomposed into a group of second-order cone programs (SOCPs) parameterized by K real parameters. Grid search or
New achievable secrecy rate regions for the two way wiretap channel
This work develops new achievable rate regions for the two way wiretap channel. In our setup, Alice and Bob wish to exchange messages securely in the presence of a passive eavesdropper Eve. In the full-duplex scenario, our achievability argument relies on allowing the two users to jointly optimize their channel prefixing distributions, such that the new channel conditions are favorable compared to that of Eve. Random binning and private key sharing over the channel are then used to exploit the secrecy advantage available in the equivalent cascade channel and to distribute the available secrecy
Reliability and Security Analysis of an Entanglement-Based QKD Protocol in a Dynamic Ground-to-UAV FSO Communications System
Quantum cryptography is a promising technology that achieves unconditional security, which is essential to a wide range of sensitive applications. In contrast to optical fiber, the free-space optical (FSO) link is efficiently used as a quantum channel without affecting the polarization of transmitted photons. However, the FSO link has several impairments, such as atmospheric turbulence and pointing errors, which affect the performance of the quantum channel. This paper proposes a quantum key distribution (QKD) scheme that uses a time-bin entanglement protocol over the FSO channel that suffers
Pagination
- Previous page ‹‹
- Page 19
- Next page ››

