Breadcrumb
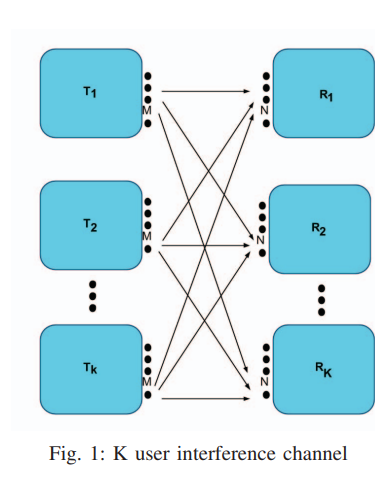
On the degrees of freedom region of the M × N Interference Channel
In this paper, the K-user MIMO interference channel is considered. The asymmetric DoF region for the channel is studied. The asymmetric DoF represent the set of all achievable DoF combinations {d1, d2,..., dK}. For the three user channel, two cases are presented, the first is when all transmitters and receivers have equal number of antennas M, the other is when each transmitter has M antennas, while each receiver has N antennas. For the K user channel, we extend our achievable scheme for the M × N case. It is assumed that the channel coefficients are constant and known to all transmitters and
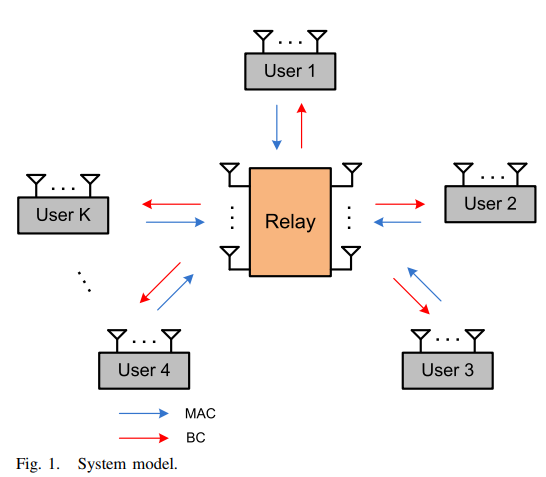
Degrees of Freedom for the MIMO Multi-Way Relay Channel with Common and Private Messages
In this paper, we study the general multiple input multiple output (MIMO) multi-way relay channel, i.e., MIMO Y channel, with common and private messages. In this channel, K users exchange messages through a common relay. Each user transmits a private message to each user in addition to a common message to all the other users. The i th user and the relay are equipped with Mi and N antennas, respectively. First, we derive the degrees of freedom (DoF) region of the symmetric three-user MIMO Y channel, where Mi = M and i ∈ {1,2,3}. Due to the symmetry of the network, we focus on the case where
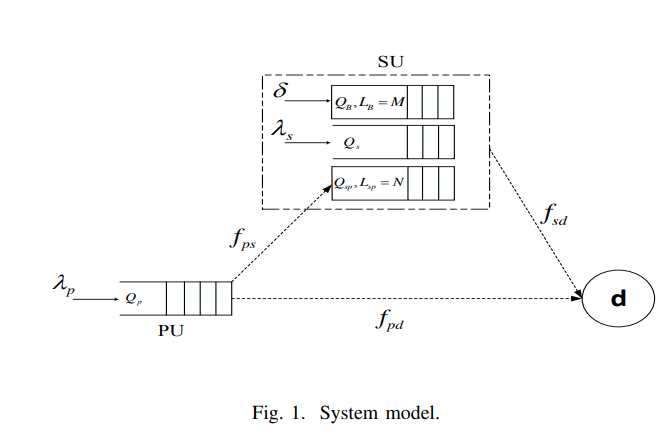
On the role of finite queues in cooperative cognitive radio networks with energy harvesting
This paper studies the problem of cooperative communications in cognitive radio networks where the secondary user is equipped with finite length relaying queue as well as finite length battery queue. The major hurdle towards fully characterizing the stable throughput region stems from the sheer complexity associated with solving the two-dimensional Markov Chain (MC) model for both finite queues. Motivated by this, we relax the problem and focus on two energy constrained systems, namely, finite battery queue with infinite relay queue and finite relay queue with infinite battery queue. We
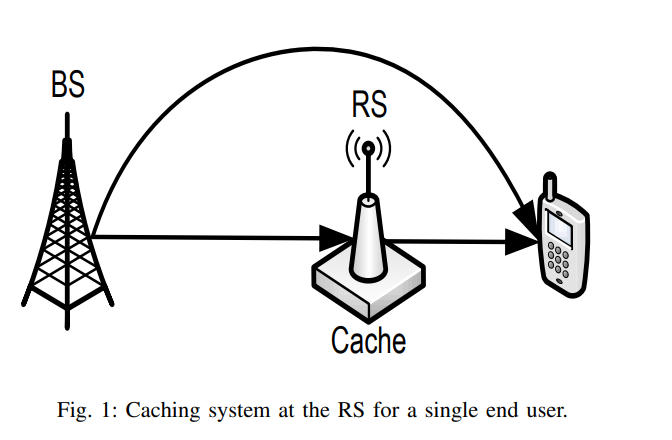
On Optimal Dynamic Caching in Relay Networks
We investigate dynamic content caching in relay networks where an intermediate relay station (RS) can adaptively cache data content based on their varying popularity. With the objective of minimizing the time average cost of content delivery, we formulate and study the problem of optimal RS cache allocation when the popularities of data content are unknown apriori to the network. While optimal dynamic cache control suffers the curse of dimensionality, we develop a fundamental lower bound on the achievable cost by any caching policy. Inspired by the structure of such lower bound, we develop a
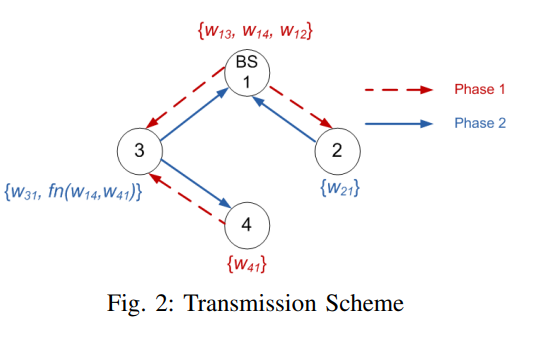
Degrees of freedom region of device-relaying cellular network
In this paper, we characterize the degrees of freedom (DoF) region of a MIMO device-relaying cellular network (DRCN) with three users and one base station (BS), where each user exchanges unicast messages with the BS. We assume that one of the users has no direct link to the BS, and hence, device-relaying is utilized to exchange data between this user and the BS, i.e., data is relayed via another user which has a direct link to the BS and a device to device (D2D) link to this user. We assume that each node operates in perfect full-duplex mode. Cut-set and genie-aided bounds are utilized to
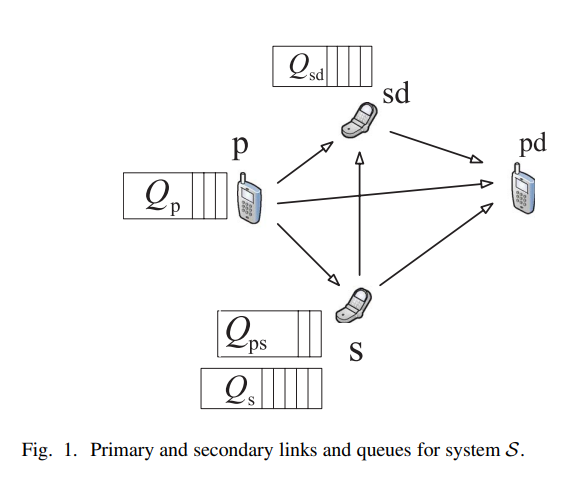
Maximum Secondary Stable Throughput of a Cooperative Secondary Transmitter-Receiver Pair: Protocol Design and Stability Analysis
In this paper, we investigate the impact of cooperation between a secondary transmitter-receiver pair and a primary transmitter on the maximum stable throughput of the primary-secondary network. Each transmitter, either primary or secondary, has a buffer for storing its own traffic. In addition to its own buffer, the secondary transmitter has a buffer for storing a fraction of the undelivered primary packets due to channel impairments. Moreover, the secondary destination has a relaying queue (buffer) for storing a fraction of the undelivered primary packets. In our proposed cooperative system
IoT Agile Framework Enhancement
Internet of Things (IoT) is considered as a trend nowadays. Devices connected to the internet interact with surrounding; this poses strong challenges in handling big data with a certain level of security. In this paper IoT devices will be divided in to two categories high vulnerability devices and low vulnerability devices. The classification depends on the ease of attacks. In order to ensure the security of IoT devices, an agile approach is used to secure high vulnerability devices as first step and then low vulnerability devices by applying encryption algorithms. © 2018 IEEE.
Cooperative cognitive relaying with ordered cognitive multiple access
We investigate a cognitive radio system with two secondary users who can cooperate with the primary user in relaying its packets to the primary receiver. In addition to its own queue, each secondary user has a queue to keep the primary packets that are not received correctly by the primary receiver. The secondary users accept the unreceived primary packets with a certain probability and transmit randomly from either of their queues if both are nonempty. These probabilities are optimized to expand the maximum stable throughput region of the system. Moreover, we suggest a secondary multiple
CellNet:A bottom-up approach to network design
The ever-increasing dependence on the Internet is challenged by several factors impeding the smooth transition to the nomadic and ubiquitous future communications. These hindering factors are primarily attributed to the top-down approach in designing computer networks that resulted in adopting a layered architecture for abstracting network functionalities as well as for engineering protocols; a methodology that proved to be neither adaptable nor evolvable in response to changes in network operational requirements and technological advancements. This paper presents a bottom-up1 strategy for
Cognitive access protocol for alleviating sensing errors in cognitive multiple-access systems
This letter studies a time-slotted multiple-access system with a primary user (PU) and a secondary user (SU) sharing the same channel resource. We propose a novel secondary access protocol which alleviates sensing errors and detects the availability of primary channels with the highest ability of detection. Under the proposed protocol, the SU may access the channel at one of a predefined instants within the time slot each of which associated with a certain access probability that changes based on the sensing outcome. There is also a possibility of accessing the channel at the beginning of the
Pagination
- Previous page ‹‹
- Page 13
- Next page ››

