Breadcrumb
A novel artificial intelligent-based approach for real time prediction of telecom customer’s coming interaction
Predicting customer’s behavior is one of the great challenges and obstacles for business nowadays. Companies take advantage of identifying these future behaviors to optimize business outcomes and create more powerful marketing strategies. This work presents a novel real-time framework that can predict the customer’s next interaction and the time of that interaction (when that interaction takes place). Furthermore, an extensive data exploratory analysis is performed to gain more insights from the data to identify the important features. Transactional data and static profile data are integrated
A Novel Deep-learning based Approach for Automatic Diacritization of Arabic Poems using Sequence-to-Sequence Model
Over the last 10 years, Arabic language have attracted researchers in the area of Natural Language Processing (NLP). A lot of research papers suddenly emerged in which the main work was the processing of Arabic language and its dialects too. Arabic language processing has been given a special name ANLP (Arabic Natural Language Processing). A lot of ANLP work can be found in literature including almost all NLP applications. Many researchers have been attracted also to Arabic linguistic knowledge. The work expands from Basic Language Analysis to Semantic Level Analysis. But Arabic text semantic
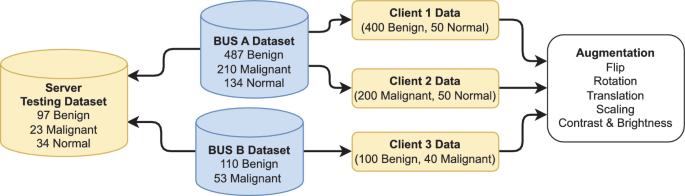
A Novel Approach to Breast Cancer Segmentation Using U-Net Model with Attention Mechanisms and FedProx
Breast cancer is a leading cause of death among women worldwide, emphasizing the need for early detection and accurate diagnosis. As such Ultrasound Imaging, a reliable and cost-effective tool, is used for this purpose, however the sensitive nature of medical data makes it challenging to develop accurate and private artificial intelligence models. A solution is Federated Learning as it is a promising technique for distributed machine learning on sensitive medical data while preserving patient privacy. However, training on non-Independent and non-Identically Distributed (non-IID) local datasets
Integrating Smart Contracts with WDNs Framework for Energy Management and Secure Transactions
The management of energy consumption and payment transactions using a secure, decentralized energy system framework is essential in the water distribution network (WDN). The water energy market, in which energy may be transformed into a digital asset that is potentially monitored, trackable and tradable, might greatly benefit from the deployment of blockchain technology. This is because the blockchain has transaction privacy, decentralization, security, and immutability features. Furthermore, using blockchain smart contracts enables energy market management operations such as consumers
SSHC with One Capacitor for Piezoelectric Energy Harvesting
Piezoelectric vibration energy harvesters have attracted a lot of attention as a way to power self-sustaining electronic systems. Furthermore, as part of the growing Internet of Things (loT) paradigm, the ongoing push for downsizing and higher degrees of integration continues to constitute major drivers for autonomous sensor systems. Two of the most effective interface circuits for piezoelectric energy harvesters are synchronised switch harvesting (SSH) on inductor and synchronous electrical charge extraction; nevertheless, inductors are essential components in both interfaces. This study
Performance Analysis of M-ary DPSK with SIMO in Ground-to-HAP FSO System in the Presence of Beam Wander and Scintillation
Studying the performance of communication systems is essential to establish a reliable and stable link with an acceptable quality of service and minimum amount of resources. This paper evaluates the ground to HAP FSO link that uses the M-ary differential phase-shift keying (MDPSK) modulation technique in the presence of turbulence and beams wandering. The performance is analyzed by comparing the Average Symbol Error Rate (ASER) with an applicable threshold of 10-4. The results confirmed that, when limiting the transmitted power to 33 dBm, which is consistent with a practical perspective, the
Qualitative Concentration Analysis of Glucose in a solution using Spectroscopic Measurement
Glucose concentration change in solution was recorded by studying transmission and absorption coefficient at different laser wavelengths, showing decrease in transmittance and increase in absorption coefficient due to increased glucose concentration. © Optica Publishing Group 2021, © 2021 The Author(s)

Energy Aware Tikhonov-Regularized FPA Technique for Task Scheduling in Wearable Biomedical Devices
Harvesting the energy from environmental sources is a promising solution for perpetual and continuous operation of biomedical wearable devices. Although the energy harvesting technology ensures the availability of energy source, yet power management is crucial to ensure prolonged and stable operation under a stringent power budget. Thus, power-aware task scheduling can play a key role in minimizing energy consumption to improve system durability while maintaining device functionality. This chapter proposes a novel biosensor task scheduling of energy harvesting-based biomedical wearable devices
Energy Optimization and Cost Reduction in Water Distribution Networks
Since the majority of energy consumed by water supply systems is used in transporting and distributing water, in addition to the energy required to pump the water from its sources, energy consumption is significantly associated with the water demand. Several studies have been carried out to optimize pump operations to achieve appropriate pressure and reduce the energy associated with controlling water levels in storage facilities. In this paper, we develop an optimization and decision support technique for a Water Distribution Network (WDN) that considers energy efficiency by limiting the
Design, Simulation & Optimization on Electrical and Optical Parameters of Alq3 QW-OLED
Although the light-emitting diode (LED) was discovered in the 1900s, it is now widely used in lighting, screens, and a variety of other indoor and outdoor applications. (Organic Light Emitting Diode) OLED is one of the advancing branches of LED technology. In the structure of Alq3 OLEDs, highlight-efficiency optical materials such as TPD (hole transport layer) and Alq3 (electron transport layer) have been used. Organic light emitting layers are between two electrical contacts. The anode was made of indium tin oxide (ITO), and the cathode was made of aluminiumlithium (Al/Li). This article
Pagination
- Previous page ‹‹
- Page 2
- Next page ››
